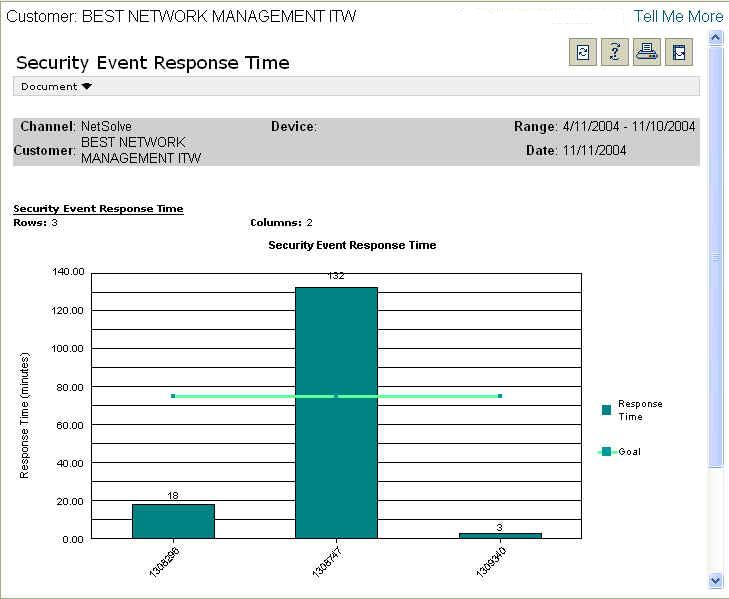
The Security Event Response Time report shows you the Time to Isolate for each security event over a specified period of time. These values appear in relation to the response time threshold value. This report allows you to view the Time to Isolate for security events that have occurred in the network.
You, your IT manager, or security expert can use this information to determine how fast we respond to security events. This graph is a performance assessment for us and shows the relative level of performance against expectations.
Report Example:

To run a Security Event Response Time report:
Select the Reports tab.
From the Available Reports categories, select Security > Security Event Response Time.
By clicking on the drop-down calendars and selecting a date or by typing over the text in the date fields, enter the date range for the report.
From the Available list, select the security event types to include in the report, and click the arrow to transfer the information into the Selected list.
Click Continue.
NOTE: You will see a message screen that shows the time until the report results
are complete. To exit the results page and send the report to the Stored Reports
page for later viewing, click Send to Stored Reports.
When viewing the report, you will see a graph containing information matching the options you selected.
For information on different ways to display and/or print report output, see Report Options.
Related topics: